Hello again, guys!
After I published my article about Telegram IM-based RAT, I've received some messages with one common point — what additional evidences can be found if a workstation being infected with Telegram IM-based RAT?
Ok, I thought, let's continue this investigation, moreover the theme had attracted such interest.

Telegram-based RAT leaves some traces in RAM and we could find it during analysis.
But in most cases an investigator can't analyse RAM in real-time mode. How can we get a RAM dump as fast as we can? For instance you may use Belkasoft Live RAM Capturer. It's completely free tool and works very fast without hard administrative efforts.

After process finished just open the dump file in any of Hex viewers (in this example I used FTK Imager, but you could choose a more lightweight tool). Do a search for telegram.org string — if a native Telegram app isn't using on the infected workstation, it's a «red flag» of Telegram RAT process presence.

Ok, let's do another search for «telepot» string. Telepot is a Python-based module for Telegram Bot API using. This is a mostly common used module in Telegram RATs.

So, now you see — it's not a big deal, especially when you know what tool is more appropriate for a task.
In Russia whole *.telegram.org domain zone is restricted by Roskomnadzor and Telegram often uses a proxy or VPN to connect to a server-side. But we can still detect DNS requests from the workstation of interest to *.telegram.org — one more «red flag» for us.
Here is the traffic sample I've taken with Wireshark:
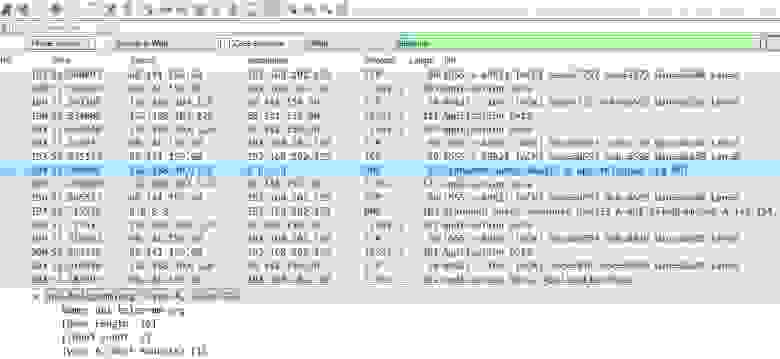
And the last but not least — Telegram RAT traces on the filesystem (NTFS here). As I mentioned in the 1st part of my article, the best way to deploy Python-based Telegram RAT using only one file is to compile all files with pyinstaller.
After the .exe file being executed, a lot of Python files (modules, libraries etc) extracted and we can find this activities in $MFT
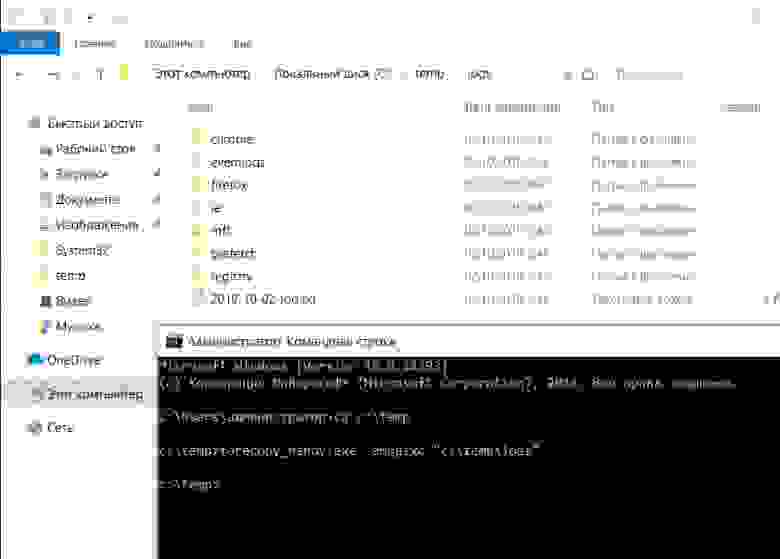
Yes, there is a free and lightweight tool to extract $MFT (and other forensically-sound things) on a LIVE system. I'm telling you about forecopy_handy tool. It's not a new-new tool, but still useful for some computer forensics do's.
Well, we can extract $MFT and, as you see, we also getting a system registry, event logs, prefetch etc
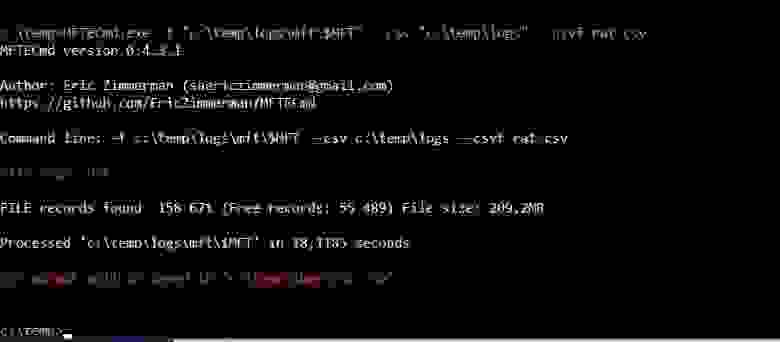
Now, let's find some traces we are looking for. We do parse $MFT with MFTEcmd
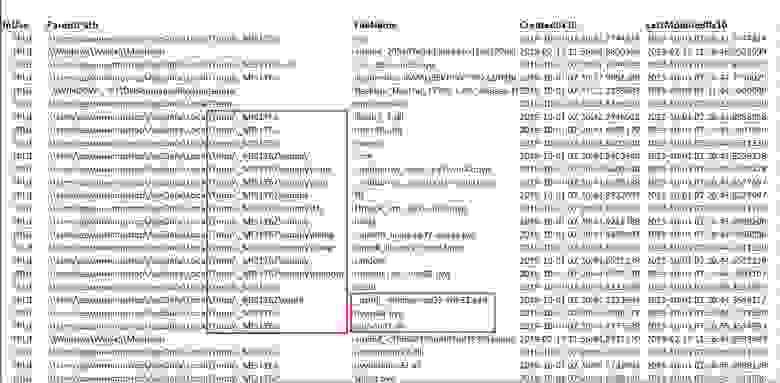
And here is the typical filesystem activity for Telegram RAT — a lot of .pyd files and Python libraries:
I think it should be enough to detect Telegram-based RAT now, guys :)
After I published my article about Telegram IM-based RAT, I've received some messages with one common point — what additional evidences can be found if a workstation being infected with Telegram IM-based RAT?
Ok, I thought, let's continue this investigation, moreover the theme had attracted such interest.

Telegram-based RAT leaves some traces in RAM and we could find it during analysis.
But in most cases an investigator can't analyse RAM in real-time mode. How can we get a RAM dump as fast as we can? For instance you may use Belkasoft Live RAM Capturer. It's completely free tool and works very fast without hard administrative efforts.

After process finished just open the dump file in any of Hex viewers (in this example I used FTK Imager, but you could choose a more lightweight tool). Do a search for telegram.org string — if a native Telegram app isn't using on the infected workstation, it's a «red flag» of Telegram RAT process presence.

Ok, let's do another search for «telepot» string. Telepot is a Python-based module for Telegram Bot API using. This is a mostly common used module in Telegram RATs.

So, now you see — it's not a big deal, especially when you know what tool is more appropriate for a task.
In Russia whole *.telegram.org domain zone is restricted by Roskomnadzor and Telegram often uses a proxy or VPN to connect to a server-side. But we can still detect DNS requests from the workstation of interest to *.telegram.org — one more «red flag» for us.
Here is the traffic sample I've taken with Wireshark:

And the last but not least — Telegram RAT traces on the filesystem (NTFS here). As I mentioned in the 1st part of my article, the best way to deploy Python-based Telegram RAT using only one file is to compile all files with pyinstaller.
After the .exe file being executed, a lot of Python files (modules, libraries etc) extracted and we can find this activities in $MFT
Yes, there is a free and lightweight tool to extract $MFT (and other forensically-sound things) on a LIVE system. I'm telling you about forecopy_handy tool. It's not a new-new tool, but still useful for some computer forensics do's.
Well, we can extract $MFT and, as you see, we also getting a system registry, event logs, prefetch etc

Now, let's find some traces we are looking for. We do parse $MFT with MFTEcmd

And here is the typical filesystem activity for Telegram RAT — a lot of .pyd files and Python libraries:

I think it should be enough to detect Telegram-based RAT now, guys :)






