As you know, some people throw a coins into a fountain or sea for a luck or for come back to this place later.

So, cyber attackers are do the same thing — they often hide some little malware agents in the IT Infrastructure to keep a possibility to come back again.
You know some of these methods:
But there is one more method to save the high-privileged permissions for further using the infected IT infrastructure — changing AdminSDholder permissions.
To understand the theoretical part of AdminSDholder you can check any article from Internet. As example try this one.
In short — there is a periodically run process in Active Directory Services which can give the permissions to a User/Group for changing security groups (e.g. Domain Admins, Schema Admins etc.) membership. To do this an attacker just need to add a User/Group to the AdminSDHolder ACL.
So, if an attacker has got a sufficient permissions to change the AdminSDHolder ACL, he can create a new User account and add this account name to the AdminSDHolder ACL.
From the article I mentioned above, you know how to check AD for this thing using Powershell.
But there is another method using YARA rule.
Every time when someone changes the AdminSDHolder ACL, a specific event 4662 being created in the Domain Controllers Security event log:

Now we can use the information from this event to create a YARA rule.
Here is it:
So, you can use this rule with Rekall/Volatility, as example, to scan the memory dump.
Thank you again for attention! I'll be back soon with a new good stuff!

So, cyber attackers are do the same thing — they often hide some little malware agents in the IT Infrastructure to keep a possibility to come back again.
You know some of these methods:
- create a new scheduled task to rerun a malware beacon periodically;
- create a new autorun key in the system registry;
- create a new system service with autostart property;
But there is one more method to save the high-privileged permissions for further using the infected IT infrastructure — changing AdminSDholder permissions.
To understand the theoretical part of AdminSDholder you can check any article from Internet. As example try this one.
In short — there is a periodically run process in Active Directory Services which can give the permissions to a User/Group for changing security groups (e.g. Domain Admins, Schema Admins etc.) membership. To do this an attacker just need to add a User/Group to the AdminSDHolder ACL.
So, if an attacker has got a sufficient permissions to change the AdminSDHolder ACL, he can create a new User account and add this account name to the AdminSDHolder ACL.
From the article I mentioned above, you know how to check AD for this thing using Powershell.
But there is another method using YARA rule.
Every time when someone changes the AdminSDHolder ACL, a specific event 4662 being created in the Domain Controllers Security event log:
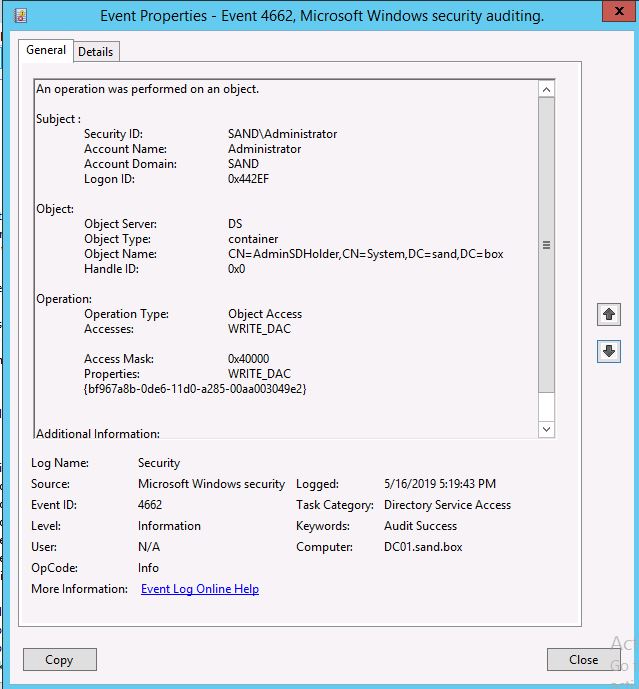
Now we can use the information from this event to create a YARA rule.
Here is it:
rule adminSDholder
{
meta:
maltype = "LuckyCoin"
reference = "https://habr.com/ru/users/volnodumcev/"
date = "17.05.2019"
description = "YARA rule to find AdminSDholder being changed by a bad guy"
strings:
$hexEventID={ 36 12 00 00 00 00 00 00 20 80 }
$object={ 7b 00 35 00 37 00 35 00 36 00 62 00 36 00 65 00 65 00 2d 00 65 00 62 00 61 00 31 00 2d 00 34 00 30 00 32 00 37 00 2d 00 38 00 32 00 39 00 64 00 2d 00 39 00 31 00 39 00 37 00 33 00 36 00 37 00 35 00 64 00 63 00 35 00 32 00 7d }
$operation={ 7b 00 62 00 66 00 39 00 36 00 37 00 61 00 38 00 62 00 2d 00 30 00 64 00 65 00 36 00 2d 00 31 00 31 00 64 00 30 00 2d 00 61 00 32 00 38 00 35 00 2d 00 30 00 30 00 61 00 61 00 30 00 30 00 33 00 30 00 34 00 39 00 65 00 32 }
condition:
$hexEventID and $object and $operation
}
So, you can use this rule with Rekall/Volatility, as example, to scan the memory dump.
Thank you again for attention! I'll be back soon with a new good stuff!